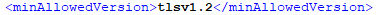How can I enforce SphereShield for SfB servers to work with TLS version 1.2?
Below are general instructions on how to enforce TLS 1.2 on the server communications in your environment:
General
You may use the following program in order to enable/disable TLS 1.0/1.1/1.2
Bastion
- Install or upgrade SQL native client version 11.0.7001.0 or higher (Download Native Client)
- Open odbcad32 and create a sql native client connection
- Modify the LAC xml\EWS protector xml file with Provider=SQL Server Native Client 11.0;
<db connStr="Provider=SQL Server Native Client 11.0; Data Source=sqlserver\instance,1433; Initial Catalog=AccessPortal; User ID=AccessPortalUser; Password=1234;" /> - In the Bastion.xml (located by default in: C:\Agat\Bastion) change the <minAllowedVersion> to tlsv1.2
- Disable TLS 1.0 and 1.1 from the system registry
- Restart bastion service or reboot the server
Edge servers
- Install or upgrade SQL native client version 11.4.7001.0 or higher
- Open odbcad32 and create a SQL native client connection (For more information about this step see below)
- Disable TLS 1.0 and 1.1 from the system registry
- Restart Sphereshield service or reboot the server
SQL Database
- Make sure you have a SQL Server version that supports TLS 1.2 (How to check which version of SQL do I have?) (Which SQL versions support TLS 1.2?)
- Install ODBC 13 on the SQL server
How to "Open odbcad32 and create a SQL native client connection":
Open a Run window and run "odbcad32"
To create a new SQL native client connection go into the "System DSN" tab and hit "New".
And then in the "Create New Data Source" window hit the "SQL Server Native client 11.0" and then hit "Finish".
From there on it's pretty straightforward. (Enter name of connection, description, server)
Note that you'll need to use SQL server authentication and not integrated windows authentication.
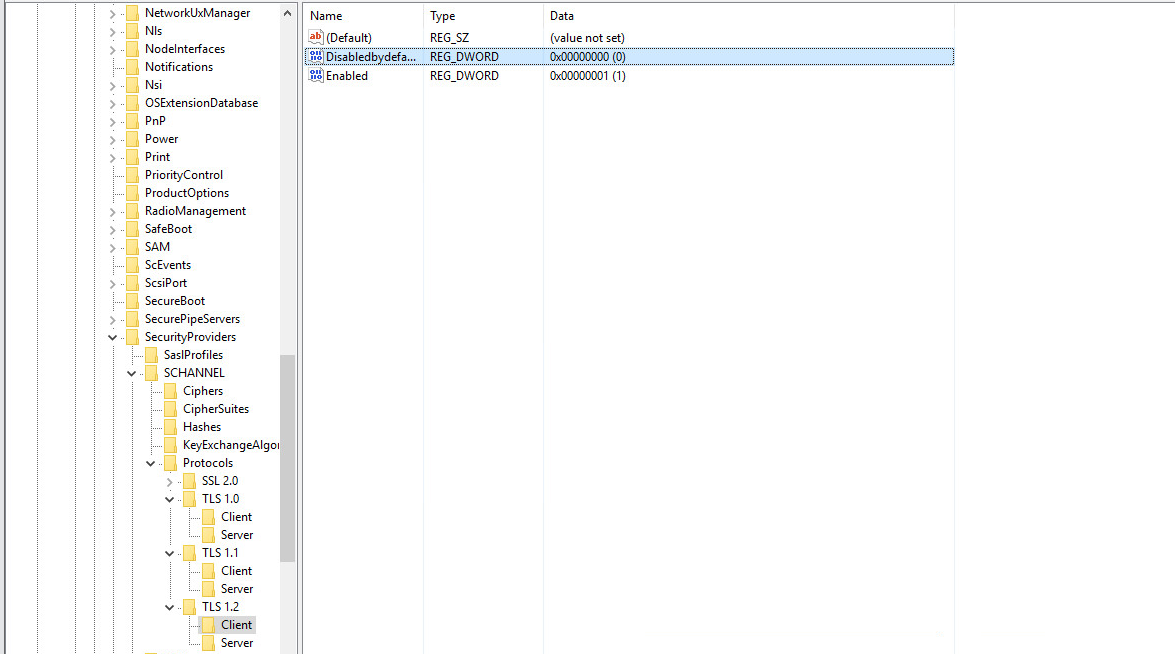
Enabling TLS 1.2 on Windows
- Open registry through the "Run" window using the command "Regedit"
- Navigate to the following location: HKEY_LOCAL_MACHINE\SYSTEM\Control\SecurityProviders\SCHANNEL\Protocols
- Make a new key and call it "TLS 1.2".
- Right-Click on TLS 1.2 and create 2 new keys. name one by the name of "Client" and one by the name of "Server"
- Make 2 new DWORD values on the "Client" and "Server" keys, call one of the values "Disabledbydefault" and the second "Enabled".
- Set the "Disabledbydefault" to 0 and the "Enabled" to 1
- Restart the machine
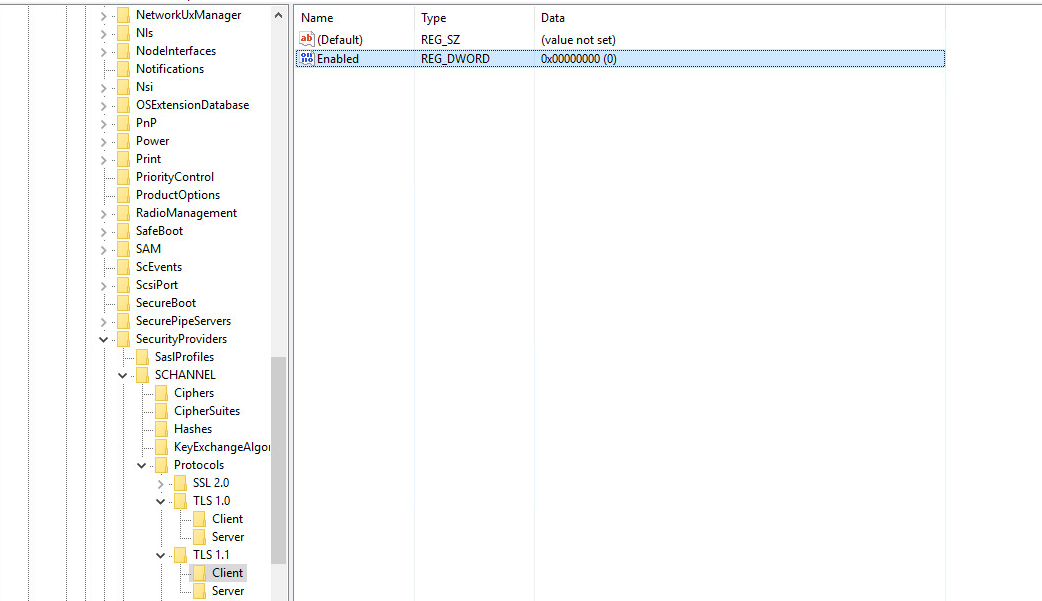
Disabling TLS 1.0 and 1.1
- Open registry through the "Run" window using the command "Regedit"
- Navigate to the following location: HKEY_LOCAL_MACHINE\SYSTEM\Control\SecurityProviders\SCHANNEL\Protocols
- Make 2 new keys. call them TLS 1.0 and TLS 1.1
- Right-Click on TLS 1.0 and TLS 1.1 and create a new key. name one by the name of "Client" and one by the name of "Server"
- Make a new DWORD value on the "Client" and "Server" keys, call the value "Enabled". and set the value to 0
- Restart the machine