MDM Integration Introduction
MDM Integration Introduction
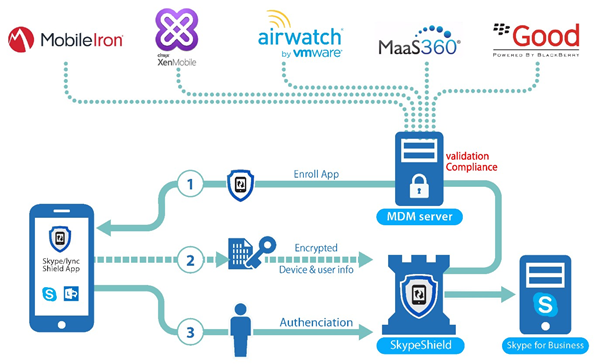
The MDM integration includes two components / Processes:
- Conditional Registration - Limit the registration only to managed devices (with MDM)- supported with all MDM vendors in the market
- Conditional Access - Ongoing validation that device is managed and has not become Out of Compliance (OOC) as defined in the MDM vendor - supported with leading vendors listed below.
For Conditional registration SphereShield for SfB offers 3 approaches:
- WIFI - Limit the registration to be done from a WIFI that requires a certificate to connect. The certificate is then managed by MDM.
- SkypeShield app- Limit the registration to be done by using a company specific SphereShield for SfB app that is only available in the corporate store/catalog to devices that are managed
- VPN - Limit the registration to be done by using a corporate VPN that only managed devices can connect to.
For conditional access, you should configure your access to your MDM server in order to get the devices synced with SphereShield database and then enable the Maintenance service to continuously validate devices.
Note that it is required to deploy conditional registration for conditional access to get the required results to avoid a situation in which an employee will register his personal device with an identical vendor & OS version to his corporate device with MDM. This will cause the HK to mistakenly match the personal device with the corporate managed device.
Background for deployment planning
The section below will explain in detail what each type of registration will mean from a topology and deployment planning standpoint as well as from the user experience standpoint. It is divided to sections, each section corresponds to a specific type of MDM integration deployment.
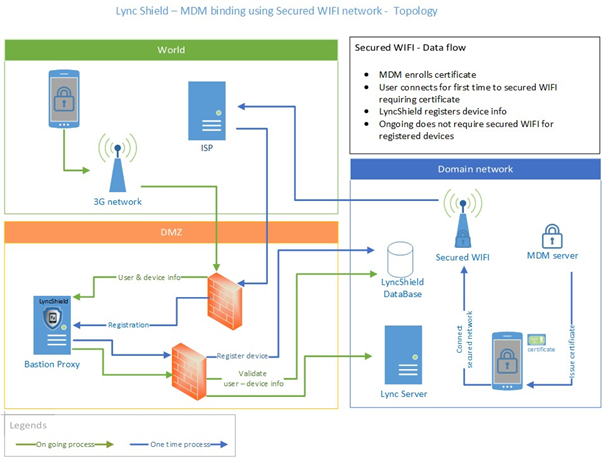
Certificate-based Wi-Fi authentication
The concept in this case is to use a certificate–secured internal WIFI network. The certificate is distributed by MDM infrastructure only, so a device cannot connect to the secured WIFI network without having the MDM installed.
SphereShield will allow only devices connecting through the secured WIFI network to enroll. Once enrolled, the device may sign in to Lync from any network connection.
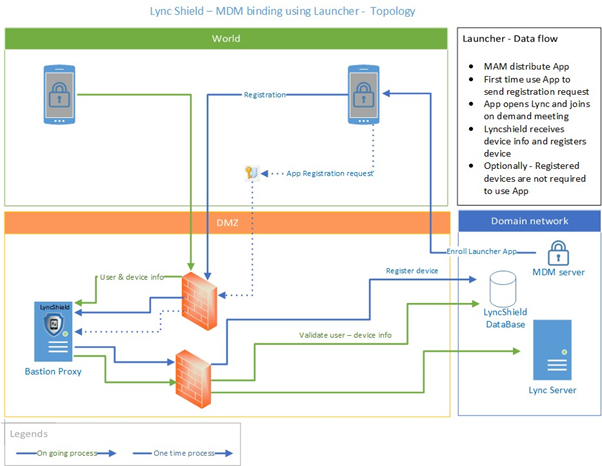
SphereShield App binding
This approach requires an App to be installed by MDM / MAM infrastructure or be available only from a corporate app store.
The app acts as a shortcut to access Lync in a secure and controlled manner.
When first used, the launcher connects securely with the SphereShield infrastructure and registers itself.
The user is then asked to press a register button in order to links the Launcher to the device’s Microsoft Lync client.
By pressing the register button, the Lync client starts and the user is connected to a system meeting that is generated automatically by SphereShield. Transparently to the user, connecting to this meeting SphereShield sends the necessary information to uniquely identify this device as being MDM managed for all future sessions.
* The app adds more security to the access process as it requires the attacker to have this company app in order to connect, in addition to DeviceID, and user credentials. The app contains a company specific Key.
The App also prevents a replay attacks using a Man in the middle by including a dynamic time stamp in the request
The app package generally consists of two files. The app itself which is a .apk file for android, or .ipa for iOS.
The second file is a text file called AppConfig.
This file contains all the configures needed by the MDM service in order to deploy the app.
App Config explanation:
- deviceId: The device id we retrieve from the MDM app. This may be UDID, IMEI etc. It depends on the MDM vendor.
- deviceIdType: Which type of id we using. e.g. for MobileIron it's UDID and IMEI (UDID|IMEI)
- username: the username that we retrieve from MDM app.
- companyName: The company name must match the one entered on the admin portal.
- defaultHost: the external lyncdiscover URL
- packageKey: A key that is used to verify that the app belongs to the company, do not change.
- skypeShieldAndroidVersion: The minimum SkypeShield Android app version for this App configuration.
- skypeShieldIosVersion: The minimum SkypeShield iOS app version for this App configuration.
In the AppConfig, there are two fields that need to be altered prior to the deployment: companyName and defaultHost.
Company name value should be exactly the same as configured in the Admin portal under MDM integration settings.
The value for default host should be the external LyncDiscover URL.
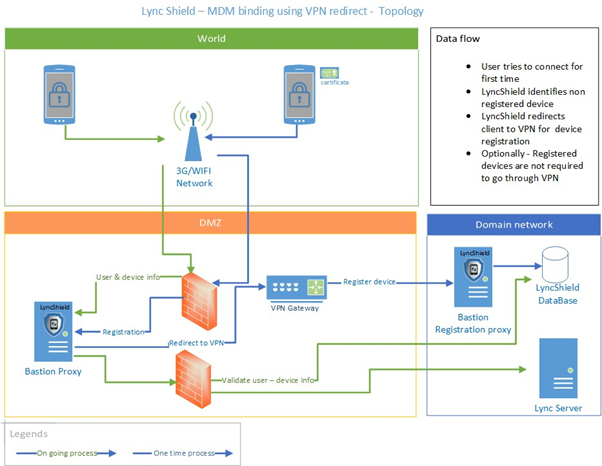
VPN redirecting
This approach requires the company to have a VPN that is only accessible from mobile devices that have an MDM client installed.
The concept of this approach is to only allow devices that are able to access the VPN to connect to Lync. This ensures that only managed devices can use Lync.
When using this approach, SphereShield will redirect any unregistered device to the VPN for registration. When the device accesses SphereShield via the VPN, the device is registered. The Lync client is then redirected to continue the remainder of the session outside the VPN.
In subsequent sessions, no VPN access will be required by the device, as the device will already be registered as MDM enabled.
In order to benefit from this approach, the company needs to have a VPN that is only accessible from MDM mobile devices. This VPN does not need to have access to the company’s LAN or internal resources.
Therefore, if a company has deployed an MDM solution and doesn’t have a VPN configured, they may set one up which only provides access to a single SphereShield server, rather than their entire internal network.
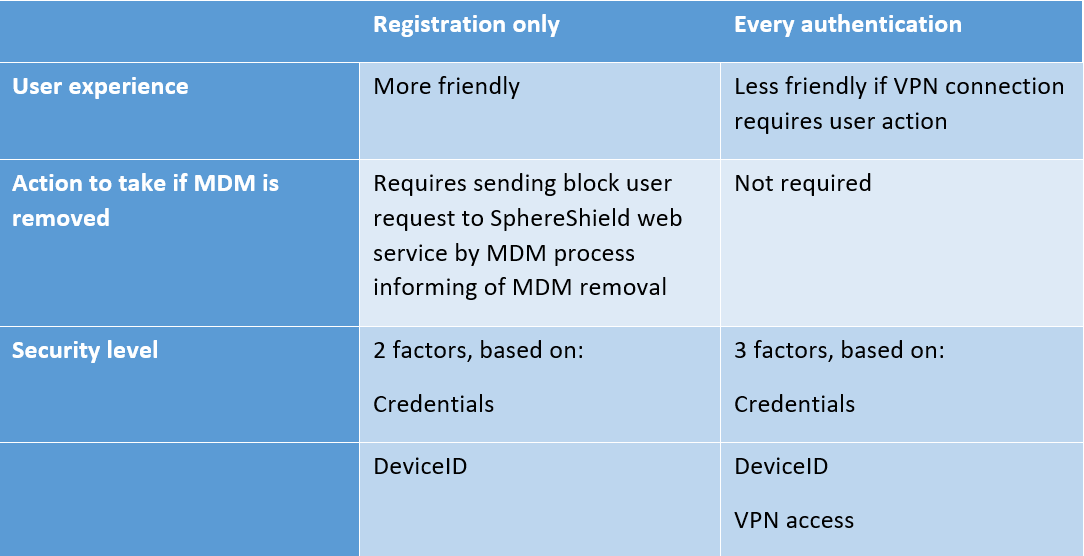
Requiring VPN for first time or on every authentication
Depending on security policy and VPN availability you can configure SphereShield to require VPN access for the registration stage only or for every sign in.
Here are the considerations related to this decision:
Device Validation
SphereShield matches device by unique device ID.
When using the app – the application sends UDID/IMEI to the Bastion and the Bastion authenticates it with the Admin Portal/DB.
When using Wi-Fi (certificate) – Only managed devices can register and SphereShield matches devices with MDM based on parameters such as user, device type, OS version…
In the rare case in which SphereShield can't do an exact match (for example user has duplicate/multiple identical devices managed in the MDM) SphereShield will block all of the devices of this type if the MDM reports on one device that it is OOC (because SphereShield cannot tell which device exactly is OOC)
Configuration instructions
Conditional Registration – WIFI access control
Please see IP filtering for restricting registration for a specific WIFI. The concept is that the will be accessible only to managed devices (by requiring a certificate) and configure SphereShield to allow the registration from this specific WIFI.
Conditional Registration – VPN
Please contact our support for assistance using this approach.
Conditional Registration - SkypeShield Launcher APP
The SkypeShield APP is an app that can be made available to your users via an MDM controlled company app store. When configured, users cannot sign in unless they open their SKYPE FOR BUSINESS client using the launcher. In this way, you can be sure that customers are only signing in from MDM controlled devices*.
*The launcher app is company specific and not available for download via Apple or Google app stores.
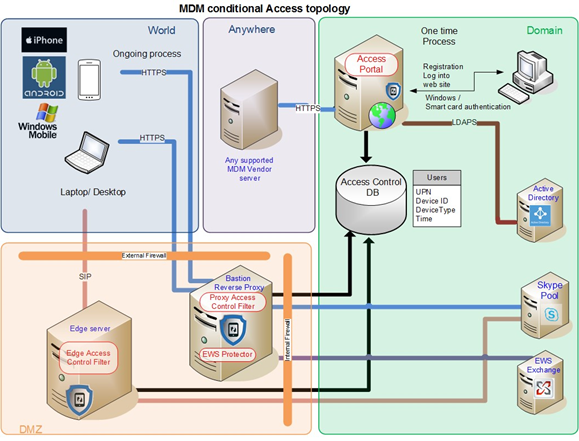
Conditional Access
The conditional registration is a one-time registration process that following them the user can use Skype for Business from any network as usual without the need to WIFI/ VPN/ SkypeShield app.
For ongoing conditional access, we have a module in the SphereShield Maintenance service services that validates devices against MDM server to make sure all SphereShield devices are managed and that none of them have become OOC.
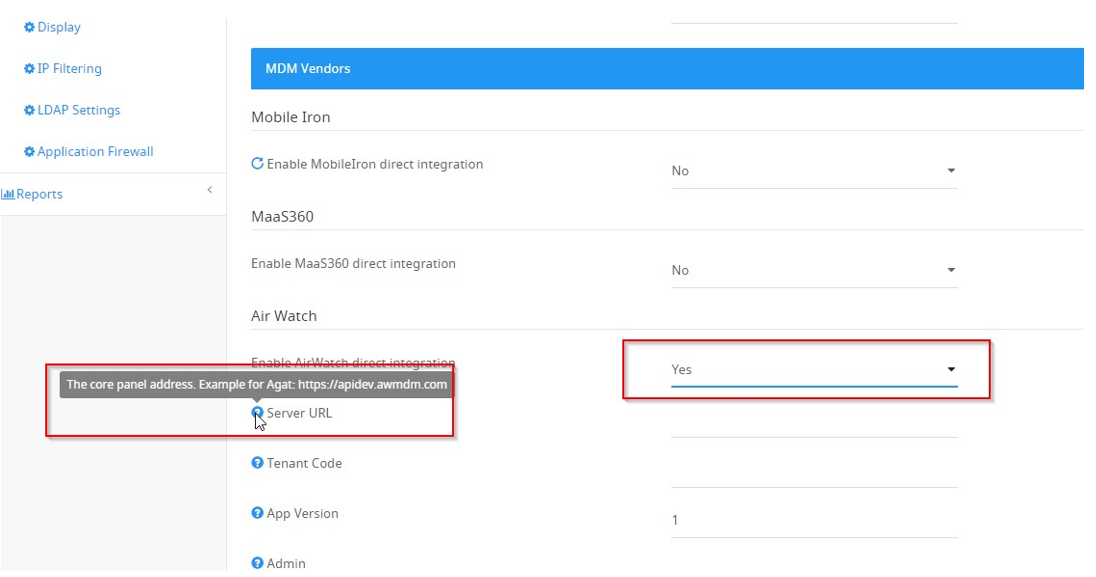
The devices registration component is available for all MDM vendors and the ongoing conditional access is available for AirWatch, MobileIron, MaaS360, XenMobile, intune, and BlackBerry.
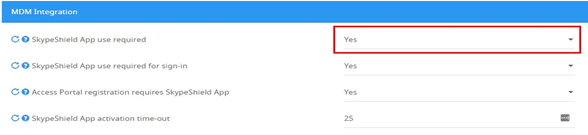
To configure conditional access – go to settings> MDM - SkypeShield app and enable the relevant MDM vendor.
Fill in the relevant values following the tooltips available in each field:
For example:
See the following section for more details on your vendor
Make sure Maintenance Service MDM settings are enabled: