How to Configure User and Group Source - LDAP Settings?
To get to the User and Group Source settings, we'll need to Sign in to the Admin Portal → Settings → User and Group Source or by using the following URL:/admin/settings?category=ldap_settings
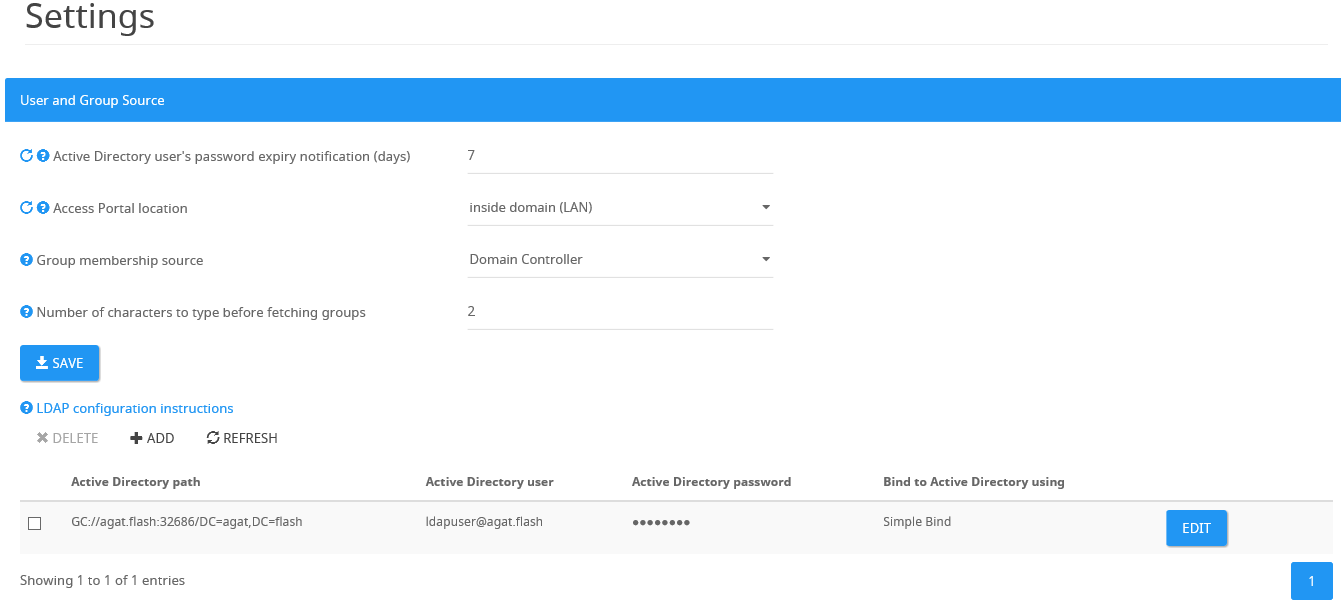
Configuring User and Group Source
Active Directory user's password expiry notification (days) - Set how many days before the Active Directory user's password (the user used for LDAP/GC connectivity) expires the system will send a notification email to the admin. To disable email notifications set to -1 .
Access Portal location - Where the Admin Portal is located - LAN or DMZ. Typically it should be in the LAN and domain-joined.
The location of the Admin Portal site affects the way group membership fetch is done. Note that when installed in the DMZ only direct group membership can be defined. Avoid using nested groups settings when the portal is in the DMZ.
Group membership source - Set the source of the Group membership. (On-premises Domain Controller, Azure Active Directory or Database)
Number of characters to type before fetching groups - Configure how many characters should be typed before starting to fetch groups. This setting is relevant for Ethical Wall, DLP rules and more.
Setting an LDAP / Global-Catalogue connection string
A restart will be required for the Maintenance Service and the IIS after reconfiguring the LDAP connection
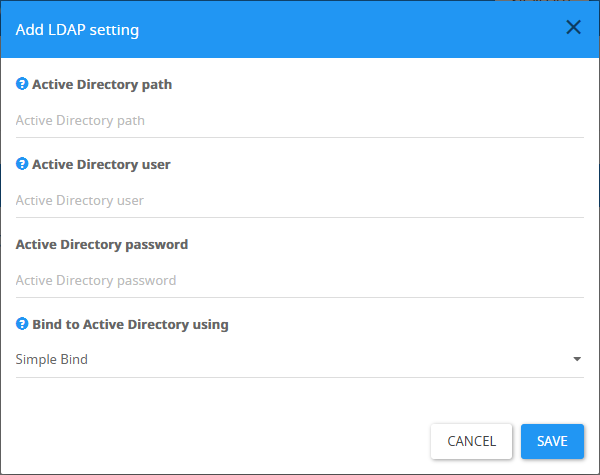
To configure a new LDAP / GC connection string select 'ADD'.
The values should be added as explained below. You can learn more about these configurations by putting the mouse on this tooltip icon next to each setting.
Active Directory path - Set the LDAP / GC path. Examples can be seen in the tooltip
Active Directory user - Always enter the username in a UPN format (user@domain.com). This Active Directory user will be used for LDAP queries. This user doesn't need to have special permissions and may be a non-administrative user.
Active Directory password - Password
Bind to Active Directory using - Set bind type (Negotiate, Negotiate with signing and sealing or Simple Bind).
Binding Methods
Simple Bind: Fastest option. Queries LDAP directly using credentials supplied. Suitable for most environments. Supports LDAP over SSL.
Negotiate: Uses Negotiate to authenticate to the LDAP server. Enables support for cross-domain trusts. Supports LDAP over SSL.
Negotiate with Sealing and Signing: Negotiate with an extra layer of protection to ensure the veracity of response. Does not support LDAP over SSL.
Forest with multiple domains
Use the global catalog to connect.
Example: GC://fabrikam.com:3268/DC=fabrikam,DC=com
Multiple forests
Use the global catalog to connect, with Negotiate binding.
You will likely require more than one connection string, one for each forest.
Where trust exists between the domains, you can connect to a single GC server, but ensure to put multiple LDAP connection string entries, each including a required Base DN (the part starting with ""DC="").
Example:
GC://fabrikam.com:3268/DC=fabrikam,DC=com
GC://fabrikam.com:3268/DC=contoso,DC=com
Notes
Port 636 (LDAP) or 3269 (GC) may be used to connect over SSL, instead of 389 or 3268.
When editing a connection, the password needs to be retyped each time.