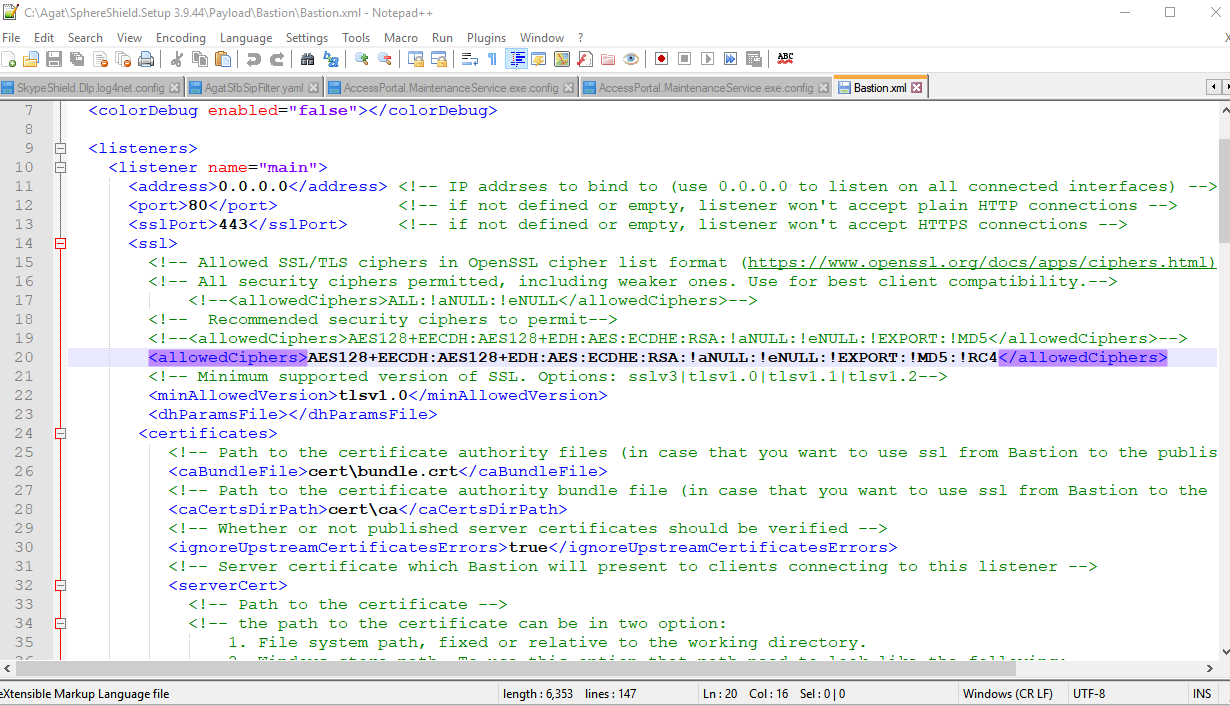
Navigate to bastion installed folder - by default c:\agat\Bastion
There open the file Bastion.XML preferable with notepad++ or other text editing software.
Scroll down to <AllowedCiphers> tag which can be found in each Listener.
All available and ignored ciphers can be found between the 'Allowed Ciphers' tags.
Putting an exclamation mark ( ! ) before a certain cipher will disable use of that particular cipher.
Colon ( : ) is used to end a list of ciphers.
When configuring ciphers, they need to be grouped together in lists ending in a colon ( : ).
The grouping is done based on which cipher suite the particular ciphers belong to.
The complete list of ciphers based on suite can be found here:
https://www.openssl.org/docs/manmaster/man1/ciphers.html
There should be separate lists for allowed ciphers and for disabled ciphers.
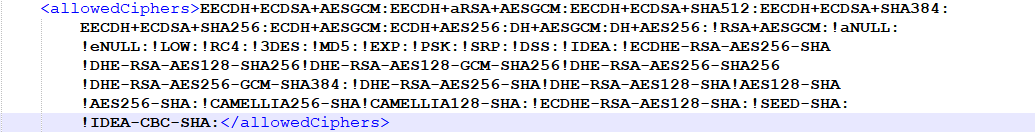
The following is an example of a more complex and hardened cipher setting:
The plus ( + ) sign between cipher names refers to ciphers using the combination of all mentioned algorithms.
For example EECDH+ECDSA +AESGCM means that ciphers using all 3 of those algorithms will be allowed.
The example !MD5: means that all ciphers using the MD5 algorithm will be disabled.
The minus sign or dash ( - ) is the openSSL name of a specific cipher.
For example !ECDHE-RSA-AES128-SHA will disable the use of the specific cipher - TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
Changing the cipher configuration should also be done according to the minimum allowed version tag <minAllowedVersion> which defines what version of TLS is allowed.
So if the minimum allowed version is tlsv1.2 then there cannot be an allowed cipher which is part of a lower version TLS cipher suite.
Once the ciphers and TLS version are properly configured, save the file and restart the Bastion reverse proxy service and it should be applied.
A recommended test would be to use https://www.ssllabs.com/ssltest/ to test the LyncDiscover URL if it is available externally.
This test will show the allowed ciphers currently in use and provide their security score.