What is DOS Protection
Publishing Skype for Business to the Internet exposes your network to DoS (Denial-of-Service), DDoS (Distributed-Denial-of-Service) and brute force attacks.
These attacks can make your network unavailable and cause significant business damage.
SphereShield blocks these attacks on the gateway level by configuring a block-failed login policy that blocks the attack attempts from reaching the Active Directory.
Configuring DOS Protection
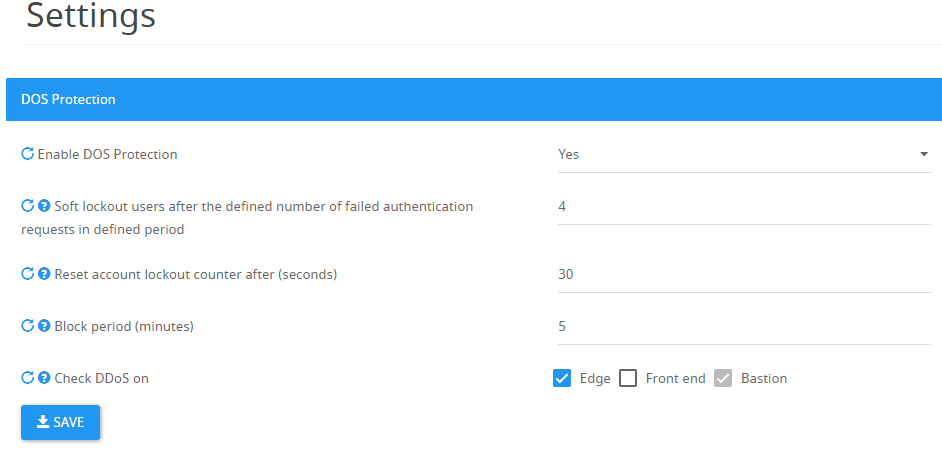
In order to get to the DOS protection settings, we'll need to sign in to the Access Portal admin area → Settings → DOS Protection, or by using the following URL:/admin/settings?category=settings_dos_protection_category_header
Soft lockout users after the defined number of failed authentication requests in defined period - How many failed authentication requests should be allowed before a soft lockout should take place. This value should be lower than the value defined in AD for "Account lockout threshold".
Reset account lockout counter after (seconds) - How much time should pass before reset the soft lockout counter and allow the blocked account to try authenticate again. This value should be slightly higher than the value defined in your AD for "Reset account lockout counter after".
Block period (minutes) - The period in which an account will be blocked (Soft Lockout) from further failed login attempts from reaching the Active Directory.
Soft Lockout is activated after reaching a number of failed attempts during the period defined by the "Reset accuount lockout counter after" value.
Should be higher than the value defined in AD for "Reset account lockout counter after
Check DDoS on - Set who besides the Bastion would check for DDoS. Typically when SIP filter is installed on the Front End for Ethical Wall, you should disable DDoS validation on the Front End as it is done on the Edge server or disable both if you don't want DOS Protection on the SIP channel.
Note:
On some mobile devices OS (i.e. Android and Windows Phones) Lync client resends login request after the failure of the first attempt with the same (incorrect) credentials. In these cases, a soft lock may occur earlier than expected.
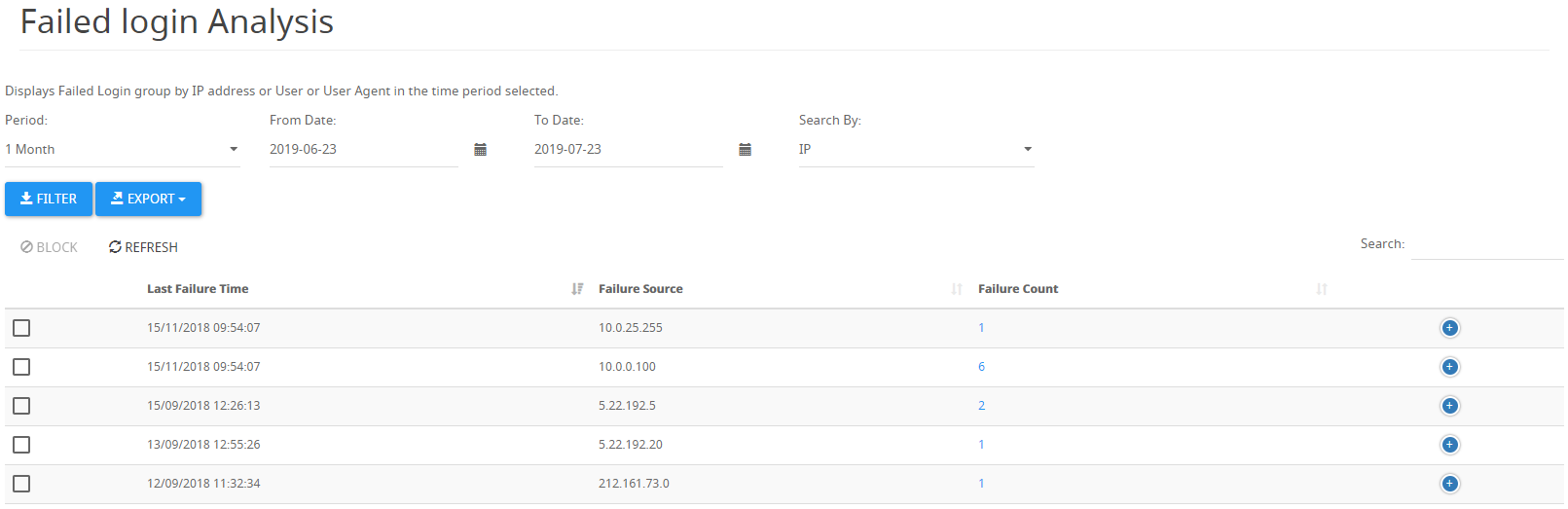
Failed login attempts
In order to monitor failed login attempts, we'll need to sign in to the Access Portal admin area → Reports → Failed Login Analysis, or by using the following URL:/admin/faildloginipreport
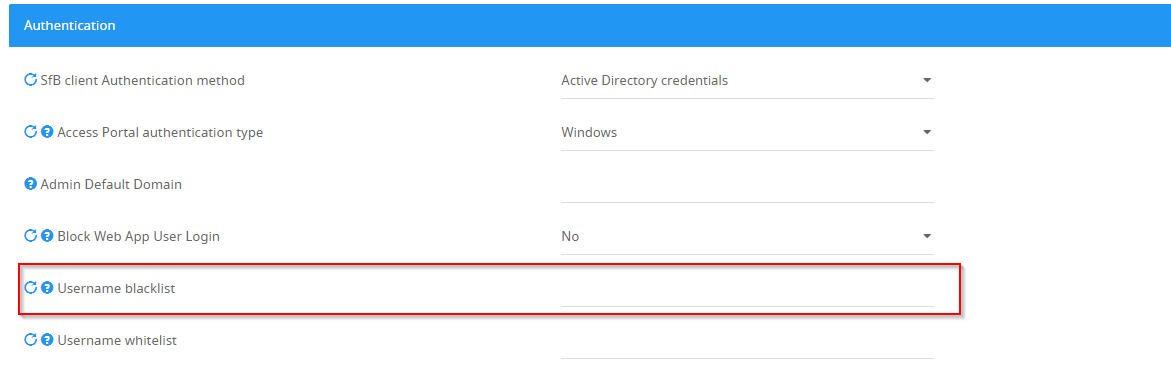
Username Patterns
The DOS Protection feature is not aware of your Active Directory Entities. Hence, bad password count for the same user in Domain\user and UPN format will be different.
For this, you need to conform to one method of username pattern and define the other in Username blacklist in Authentication settings.