Introduction
SphereShield is a security platform designed to let companies deal with access control, compliance and threat protection. The SphereShield platform is based on a proprietary proxy with extendable multi-protocol filtering capabilities and an admin site for product management, reporting and configuration.
SphereShield for Teams is a security suite tailor-made for Microsoft Teams, designed to protect the Microsoft Teams environment using a CASB approach
AGAT Software offers a sandboxed demonstration environment to demonstrate the abilities of SphereShield for Teams.
What is a CASB?
CASB (Cloud Access Security Broker) is a security product made to handle the security challenges introduced by utilizing a software solution in the cloud.
CASB is usually offered in 3 flavors:
- Adapter API - a service connecting to APIs exposed by the Cloud Service provider without intercepting traffic.
- Reverse Proxy - a proxy server that intercepts traffic sent directly to it and responds as a server.
- Forward Proxy - a proxy server configured on a client device to intercept traffic sent to any of the hosts configured for inspection.
These options can be used together or individually for different purposes. Each option has its own benefits and limitations.
For full protection including Data-in-Motion and mobile apps - you should utilize all three modules of the SphereShield for Teams product suite.
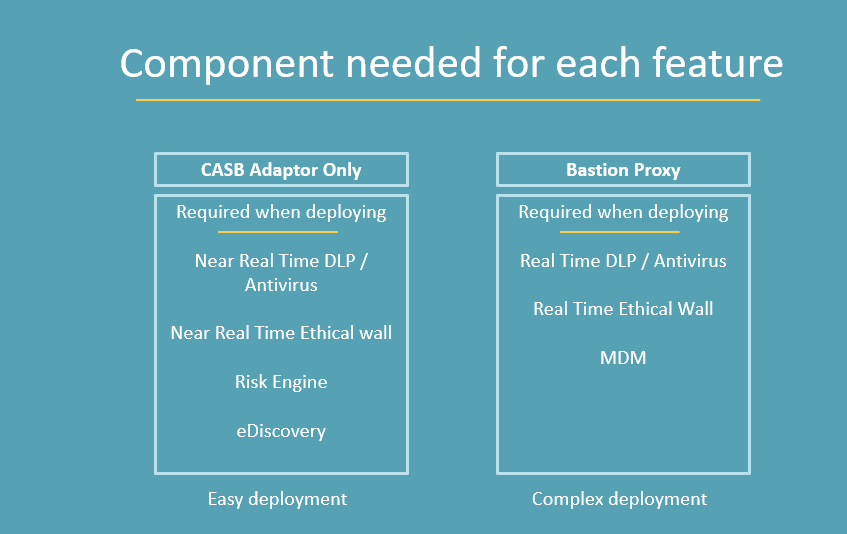
Comparison of CASB approaches
Feature comparison
Note: When deploying Ethical Wall, the Proxy must be used to block Search, Audio, Video and Screen sharing.
API Vs Proxy : Further comparison
| API | Proxy | |
|---|---|---|
Real Time (DLP and Ethical Wall) | X (will delete content within seconds) | V (will block communication from reaching the cloud) |
| Ethical Wall | ||
| Block Search | X | V |
| Chat | V | V |
| Files | V | V |
| Audio | X | V |
| Video | X | V |
| Screen share | X | V |
| Remove users from Teams/Chat | V | X There is no need to do this with the proxy approach since all communication can be blocked at source |
| Block remote control in meeting | X | V |
| Block user from being Guest in external tenant | X | V |
| eDiscovery | ||
| Chat messages and files | V | X |
| Meeting events | X | V |
| Screen share events | X | V |
eDiscovery using Proxy and API components
For Full eDiscovery both proxy and API are needed.
The API can get info on Chat and Files.
The proxy can get info on Audio, Video, Desktop sharing and meeting participants
Deployment can support having both Proxy and API components.
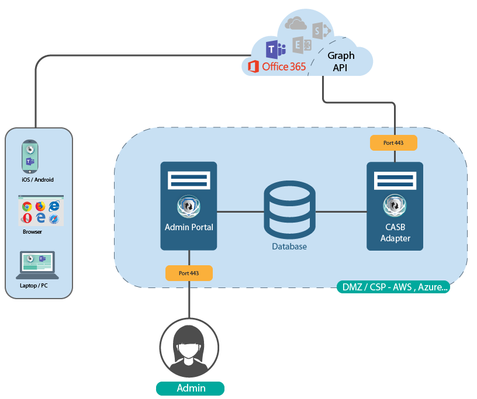
Adapter API Topology
This topology is the most simple to implement and is recommended to start with.
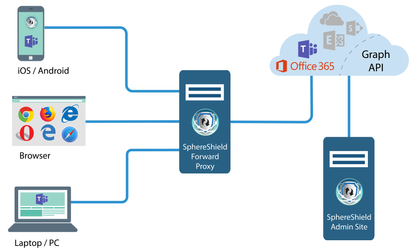
Forward Proxy topology
SphereShield for Teams as a Forward Proxy protects MS Teams mobile apps, MS Teams browser access, and MS Teams desktop client.
It can be configured as a global proxy using an MDM/EMM solution or using proxy chaining with an existing Forward Proxy or Security Gateway.
SphereShield for Teams as a Forward Proxy does not require ADFS or any other IdP to redirect the traffic to the proxy.
Distribution of the SphereShield Root CA to end-user devices is required in order to implement this solution.
Reverse Proxy topology (requires ADFS)
SphereShield for Teams as a Reverse Proxy protects MS Teams browser access and MS Teams desktop client.
It is an agent-less solution that does not require any changes on the end user device.
It does require use of ADFS or another IdP in order to redirect the traffic to the SphereShield Reverse Proxy.
SphereShield Reverse Proxy must reverse proxy ADFS traffic to provide the necessary client redirection.
What does the CASBA (API) module offer?
SphereShield for Teams Cloud Access Security Broker Adapter (CASBA) communicates with the Office 365 API.
It does not require any changes on the end user device and does not inspect Data-in-Motion.
SphereShield for Teams CASBA does not require ADFS or any other IdP to redirect the traffic to the proxy.
Note: A Key Vault subscription is required in the Azure tenant to securely store keys used by the application. This is a free subscription by Microsoft.


.png?version=1&modificationDate=1545649744936&cacheVersion=1&api=v2&width=414&height=250)

