How to Configure Risk Engine?
The Risk Engine section in the Admin Portal has 3 pages:
- Geolocation Live Map - view logins attempts and filter them by username, activity type and period.
- Geolocation Fencing - configure geolocation policies which enable location-based access restriction.
- Risk Engine under Settings - configure the Risk Engine.
Risk Engine Settings
1. Geolocation Google Map Key - The Key that will be used in the request to Google Map API. Click here for Google's guide on how to get the key.
2. Maximum number of users to retrieve in map - The number of records that should be displayed on the map. Leaving this field empty to display all records. This might cause long loading times.
3. Enable Geo Fencing - Enable the ability to defines from which country users are allowed to sing in.
4. Calculated policy cache validity period (hours) - For how many hours the policy should be valid. Set to a high number if no changes are expected to be made in the groups or rules.
5. Policy rules memory cache time (minutes) - For how many minutes the policies should be cached in the memory. Small values can impact performance.
6. Geo Fencing incident notification - Type of notification to send upon a Geo-Fencing incident. You can choose none, Mail, Mail and IM.
7. The Email address of the recipient to send a notification upon Geo-Fencing incident.
8. The SIP address of the recipient to send a notification upon Geo-Fencing incident.
9. The subject of the notification Email.
10.The content of the notification IM message.
11.
12.
13.
14.
15.
16.
17.
18.
19.
20.
Geolocation Live Map
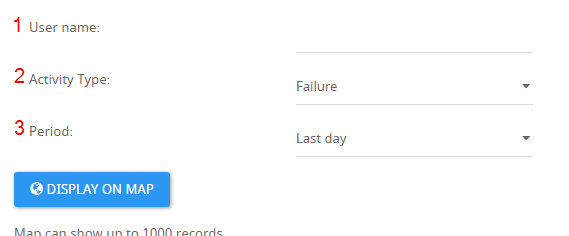
1 - User name to search for.
2 - The type of activity you wish to display. You may select one of the following:
Success - shows location and data of any successful signin
Failure - shows location and data of any bad credential attempts or attempts from an unapproved device
Risky - shows location and data of any attempt from an IP that has bad IP reputation. For example due to password spraying attack
3 - The time period from which to start collecting the information.
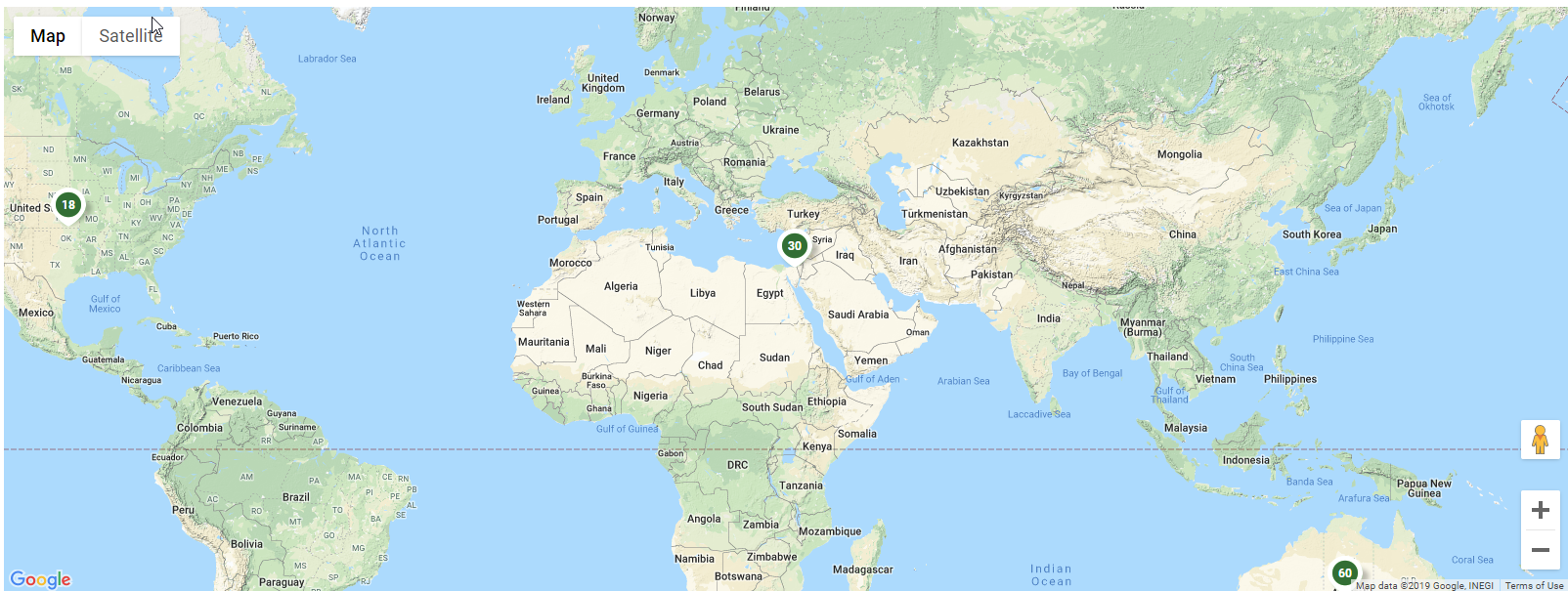
In the following example, we can view all successful sign in attempts from the last year:
Geolocation Fencing
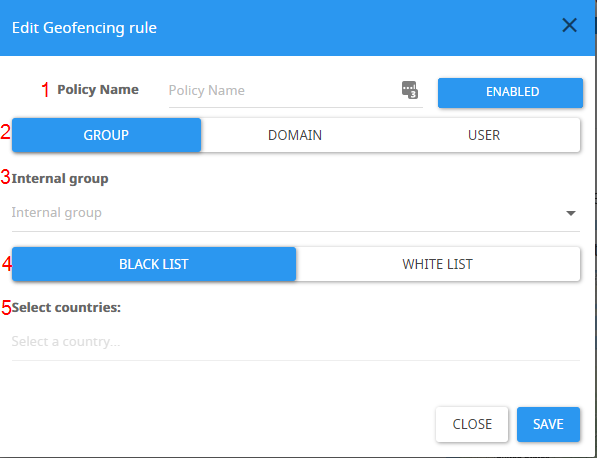
1 - The name of the policy
2 - Whether to apply the policy to a certain AD group/user or domain
3 - The group/user/domain to apply this policy to.
4 - Whether this policy will white list or blacklist login attempts.
5 - The countries that are relevant to this policy.